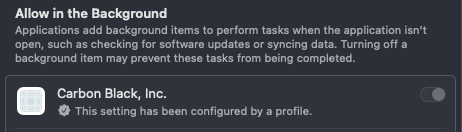
With the profile earlier in the series, a admin user would be able to disable Carbon Black from running in the background and so, stop it from running all together.
So, let us add two extra options to the profile by adding a version.
Open the profile and look for “Login Items”. Here you want to add Carbon Black to the applications section.
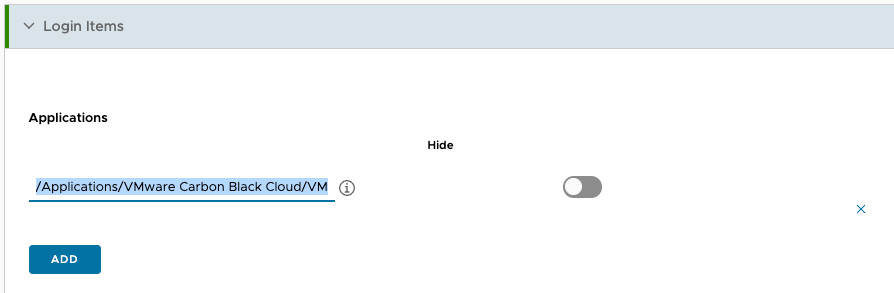
The second part is under the “Login and Background Items” section. Allow Carbon Black to run in the background based on the Team Identifier.

For me, this resulted in an error and it seems to be a bug in the interface.

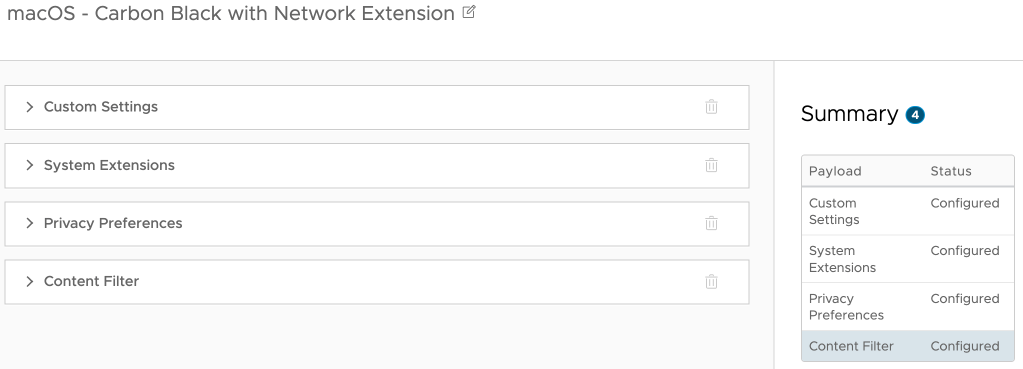
Go to the “System Extensions” section and remove the parts that are not in use. Heads up, they will get added again on saving the profile.

That’s it. Save and assign and you are good to go. Hope this helps!