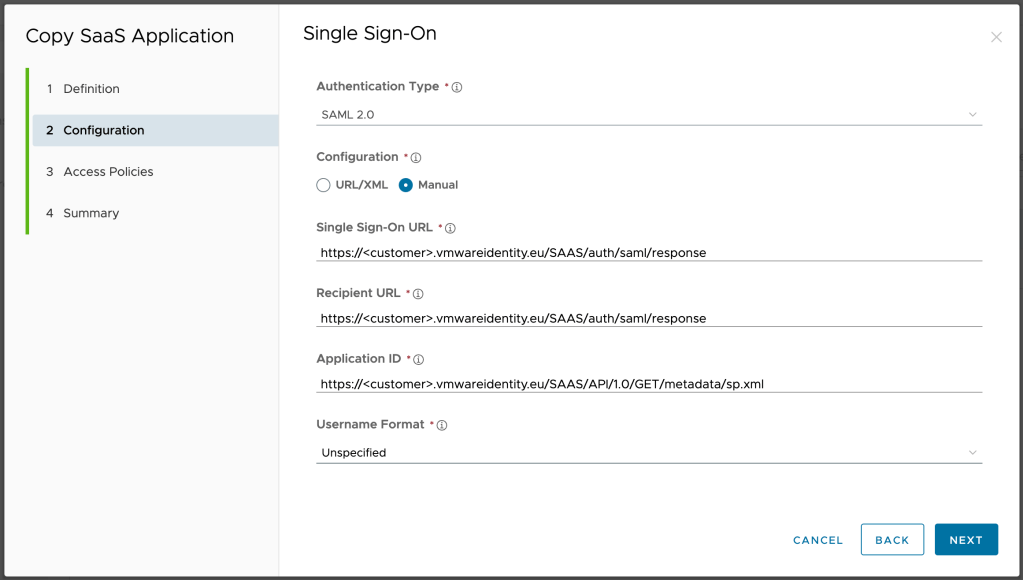
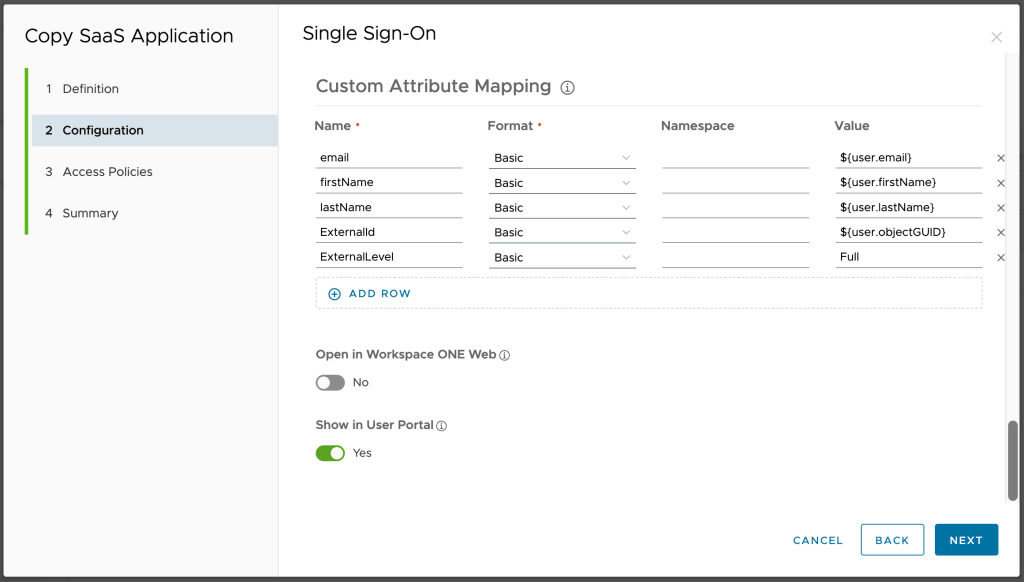
Now that we are done on our side, the customer side is next. First step is to create a custom attribute that we used in our tenant to hold the static text. Goto settings > user attributes, add a row to the custom attributes and name it ExternalLevel.

Now allow just-in-time user provisioning by creating a new identity provider. Name the IdP and past in SAML metadata URL. Next Process IdP metadata.

Enable just-in-time provisioning and name your new directory.

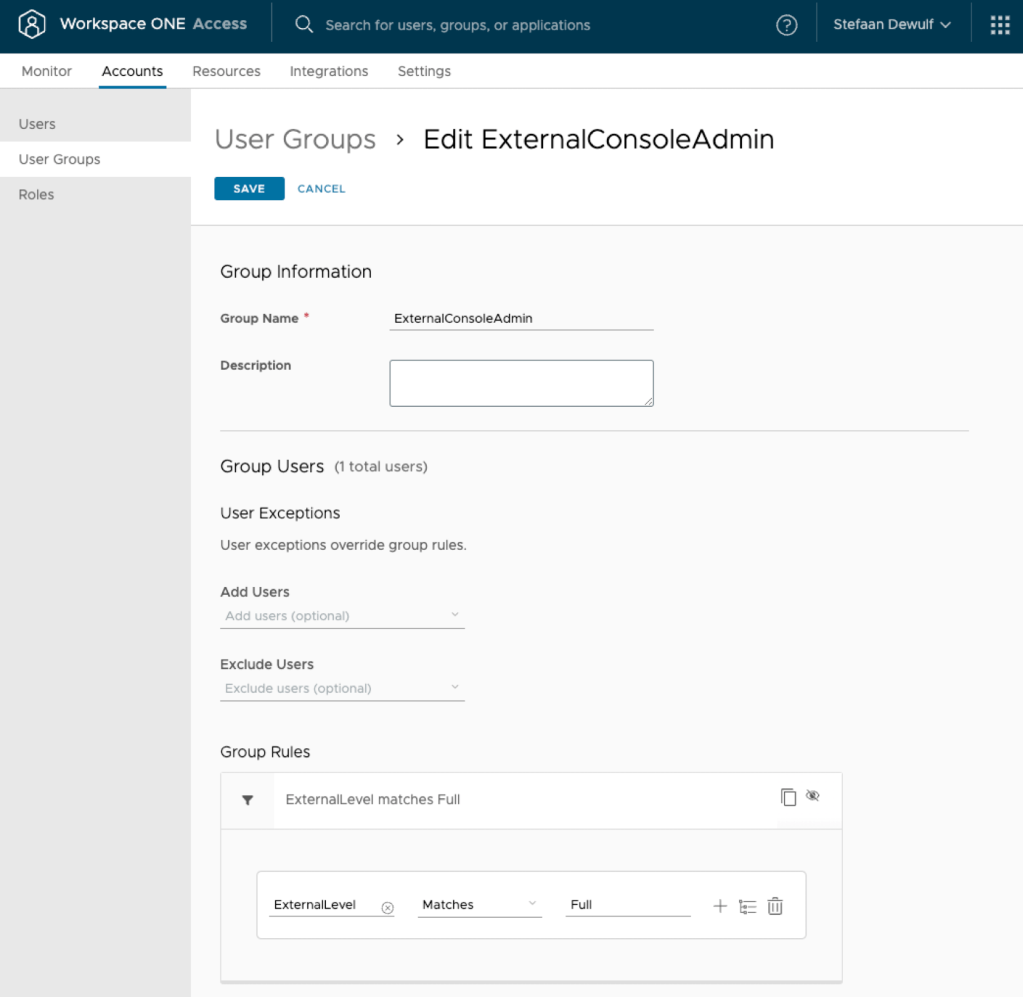
Next, create two groups and assign the correct roles based on the ExternalLevel attribute.

The final step, often forgotten, is to allow authentication using the new IdP in the necessary policy rules.